|
Beware Of Downloading Pretty Things On The Web
Have you ever misplaced or neglect a password to a highly safe file,which is extremely necessary for you and allow you to in a big bother. I feel almost every pc customers would have encountered such did i,that is one reason why I refuse to password protect my pc and files earlier than.Leaving the computer and recordsdata unrestricted shouldn't be the solution.I feel the perfect resolution is to find a glorious password restoration utility to unlock the password -protected laptop or recordsdata after we forgot or lost it.
 Dictionary assault means that you can take away RAR password in accordance with default dictionary of this system, besides, you'll be able to add your own dictionary to the program with a purpose to shorten the RAR password restoration time. The best way to Take away Password Protection on WinZip Remove Password – after you may have chosen the password protected file click this second button. Did you ever make a cross protected winrar file and by the time you needed to open it, you forgot the password? So did we and that's the reason we developed this winrar archive unlocker. It's available for anybody to obtain totally free! We don't ask our users for cash, so that everyone can use it. We solely ask our customers to obtain it from certainly one of our sponsored survey links. Open an encrypted archive within WinRAR.
Dictionary assault means that you can take away RAR password in accordance with default dictionary of this system, besides, you'll be able to add your own dictionary to the program with a purpose to shorten the RAR password restoration time. The best way to Take away Password Protection on WinZip Remove Password – after you may have chosen the password protected file click this second button. Did you ever make a cross protected winrar file and by the time you needed to open it, you forgot the password? So did we and that's the reason we developed this winrar archive unlocker. It's available for anybody to obtain totally free! We don't ask our users for cash, so that everyone can use it. We solely ask our customers to obtain it from certainly one of our sponsored survey links. Open an encrypted archive within WinRAR. Winrar password remover uses many new algorithms that successfully and quickly break the password. Spidery algorithm and formic acid are used within the software. Winrar password remover is quick as a result of the program makes use of multi-threading. The multi-threading uses the full energy of the processor to decrypt password of any file. The program performs a number of operations at the similar time, by which the decrypt password is way smaller as compared to different packages of this type. Winrar password remover help for an algorithm, up to one hundred operations at the same time, multi-threading and it is very easy to use. Winrar password remover makes use of two strategies with a view to bypass Winrar passwords.
Winrar password remover uses many new algorithms that successfully and quickly break the password. Spidery algorithm and formic acid are used within the software. Winrar password remover is quick as a result of the program makes use of multi-threading. The multi-threading uses the full energy of the processor to decrypt password of any file. The program performs a number of operations at the similar time, by which the decrypt password is way smaller as compared to different packages of this type. Winrar password remover help for an algorithm, up to one hundred operations at the same time, multi-threading and it is very easy to use. Winrar password remover makes use of two strategies with a view to bypass Winrar passwords. Forgetting a password for an archive created long time ago is a standard annoyance. RAR Password Recovery helps you to get your knowledge back. Superior dictionary attack, brute-power attack, and superior brute-pressure with mask assault are used to get well the password This software program is straightforward to put WinRar Mot de passe Retirez 2014 in and straightforward to make use of. All it's essential to do to recover your password is just to drag and drop your file to this system window. Dictionary attack helps 'mistypes' and extra user dictionaries.
Forgetting a password for an archive created long time ago is a standard annoyance. RAR Password Recovery helps you to get your knowledge back. Superior dictionary attack, brute-power attack, and superior brute-pressure with mask assault are used to get well the password This software program is straightforward to put WinRar Mot de passe Retirez 2014 in and straightforward to make use of. All it's essential to do to recover your password is just to drag and drop your file to this system window. Dictionary attack helps 'mistypes' and extra user dictionaries. RAR Signal Snapper should get well mislaid safety passwords supposed for RAR/WinRAR racks. RAR Safety password Get collectively christmas cracker picks up moreover "bruteforce", as well as "dictionay" ("wordlist") tactic. Private used-acquiring data in addition to multivolume microfilm are usually assisted. RAR Security password The vacation season get together cracker might help to preserve a preexisting indicate (you are able to lower off this course every time they need, together with continue from your comparable state subsequently).
With this RAR password remover, all you might want to do to get better your password is just to tug and drop your file to this system window. Following is a simple information to take away RAR password How you can Bypass the Password on Home windows XP after we lose RAR file password. If in case you have any doubts in regards to the RAR password cracker , you possibly can CLICK ON RIGHT HERE for more detailed info. Final however not least, do not lose the RAR password once more. How you can Put a Password on Winrar RAR Password Restoration Magic is very easy to use. To recover a password, all it is advisable do is simply so as to add your file to the operation window. E-signature key hacking Atomic RAR Password Recovery is a software designed to restore the password for the archives created by WinRAR archiver cracking winrar password protection
RAR Signal Snapper should get well mislaid safety passwords supposed for RAR/WinRAR racks. RAR Safety password Get collectively christmas cracker picks up moreover "bruteforce", as well as "dictionay" ("wordlist") tactic. Private used-acquiring data in addition to multivolume microfilm are usually assisted. RAR Security password The vacation season get together cracker might help to preserve a preexisting indicate (you are able to lower off this course every time they need, together with continue from your comparable state subsequently).
With this RAR password remover, all you might want to do to get better your password is just to tug and drop your file to this system window. Following is a simple information to take away RAR password How you can Bypass the Password on Home windows XP after we lose RAR file password. If in case you have any doubts in regards to the RAR password cracker , you possibly can CLICK ON RIGHT HERE for more detailed info. Final however not least, do not lose the RAR password once more. How you can Put a Password on Winrar RAR Password Restoration Magic is very easy to use. To recover a password, all it is advisable do is simply so as to add your file to the operation window. E-signature key hacking Atomic RAR Password Recovery is a software designed to restore the password for the archives created by WinRAR archiver cracking winrar password protection
How To Cease Your Hotmail Email Account From Being Hacked?
Outlook Specific can is likely one of the greatest email clients on the market with its easy to navigate interface and helpful features and in addition Hotmail when of the most effective e-mail program on the web. So what when you may take these two nice packages and synchronize them collectively? Subsequently once you get an email out of your Hotmail account your get a notification for Outlook Categorical.
 Gmail is probably the most generally used internet-based e mail service that has over 425 million energetic users worldwide as per a June 2012 survey. It affords some superb features along with its e-mail that add to the recognition of it, and make it most famous all across the world. Google also works on Gmail's safety service so that individuals don't get nervous about their email's security. Password is a very powerful safety function and it is very important that it ought to always be protected. When a user forgets his password because of any purpose, it might be a very laborious time for him and he might begin for tactics to retrieve it.
Gmail is probably the most generally used internet-based e mail service that has over 425 million energetic users worldwide as per a June 2012 survey. It affords some superb features along with its e-mail that add to the recognition of it, and make it most famous all across the world. Google also works on Gmail's safety service so that individuals don't get nervous about their email's security. Password is a very powerful safety function and it is very important that it ought to always be protected. When a user forgets his password because of any purpose, it might be a very laborious time for him and he might begin for tactics to retrieve it. Easy methods to Keep away from Being Hacked on Facebook The right way to Fix a Hacked Computer Methods to Create a New E-mail Address With Hotmail The free e mail hacker program might make it occur for you. The hacker might need entry to your laptop. Go to Hotmail and sign in into your Hotmail The way to Know If Someone Hacked Your Telephone Now, send this Hotmail file to victim of which you wish to hack Hotmail password and convince him that this program can hack anybody's Hotmail passwords. hotmail password restoration Once E mail Hacker is put in in your system, issues get even simpler! All it's important to do is choose the desired email service supplier you need hacked by ticking the appropriate field, on this case you wish to hack a Hotmail password so tick the Hotmail field. Methods to crack hotmail Password?
Easy methods to Keep away from Being Hacked on Facebook The right way to Fix a Hacked Computer Methods to Create a New E-mail Address With Hotmail The free e mail hacker program might make it occur for you. The hacker might need entry to your laptop. Go to Hotmail and sign in into your Hotmail The way to Know If Someone Hacked Your Telephone Now, send this Hotmail file to victim of which you wish to hack Hotmail password and convince him that this program can hack anybody's Hotmail passwords. hotmail password restoration Once E mail Hacker is put in in your system, issues get even simpler! All it's important to do is choose the desired email service supplier you need hacked by ticking the appropriate field, on this case you wish to hack a Hotmail password so tick the Hotmail field. Methods to crack hotmail Password? Please be aware that, in line with Home windows Reside Crew, a brief Windows Live Solution account will be created for you. The momentary account means they will setup a non-public forum the place you may discuss the compromised hotmail account with their assist Pirater mot de passe Hotmail 2014 agent. Your answers to reset or recuperate the hacked hotmail password or account can be stored within the private discussion board. You may return to the discussion board to examine the standing of their investigation. It is basically just a assist ticket through a brief Home windows Reside Resolution account.
Please be aware that, in line with Home windows Reside Crew, a brief Windows Live Solution account will be created for you. The momentary account means they will setup a non-public forum the place you may discuss the compromised hotmail account with their assist Pirater mot de passe Hotmail 2014 agent. Your answers to reset or recuperate the hacked hotmail password or account can be stored within the private discussion board. You may return to the discussion board to examine the standing of their investigation. It is basically just a assist ticket through a brief Home windows Reside Resolution account. So far as service management is concerned, outlook buyer support additionally go away no stone unturned to provide steady and hurdle-free service to the customers. A problem like password restoration or one thing more intricate as hacked outlook account could be resolved with the assistance of official professionals. Other than the official Microsoft service workforce, the users can search assist from third parties as nicely. How to Add a Image Background to a Hotmail E mail Incoming & Outgoing Server Settings for Hotmail in Outlook How one can Access Dwell Hotmail With Thunderbird The best way to Speed Up Hotmail How you can Disable Hotmail Google tells that it's not their servers which were hacked , but they assume it is phishing technique that has been used in the direction of their users. Why Has Hotmail Crashed?
So far as service management is concerned, outlook buyer support additionally go away no stone unturned to provide steady and hurdle-free service to the customers. A problem like password restoration or one thing more intricate as hacked outlook account could be resolved with the assistance of official professionals. Other than the official Microsoft service workforce, the users can search assist from third parties as nicely. How to Add a Image Background to a Hotmail E mail Incoming & Outgoing Server Settings for Hotmail in Outlook How one can Access Dwell Hotmail With Thunderbird The best way to Speed Up Hotmail How you can Disable Hotmail Google tells that it's not their servers which were hacked , but they assume it is phishing technique that has been used in the direction of their users. Why Has Hotmail Crashed? Sadly for Twitter, Hacker Croll found such a weak point. An worker who has on-line habits that are in all probability no completely different than those of 98% of other web customers. It began with the personal Gmail account of this employee. As with most other internet functions, the personal edition of Gmail has a password restoration feature that presents a user with a number of challenges to prove their id so that their password will be reset. On requesting to get better the password, Gmail knowledgeable him that an electronic mail had been sent to the consumer's secondary e mail account.
Sadly for Twitter, Hacker Croll found such a weak point. An worker who has on-line habits that are in all probability no completely different than those of 98% of other web customers. It began with the personal Gmail account of this employee. As with most other internet functions, the personal edition of Gmail has a password restoration feature that presents a user with a number of challenges to prove their id so that their password will be reset. On requesting to get better the password, Gmail knowledgeable him that an electronic mail had been sent to the consumer's secondary e mail account.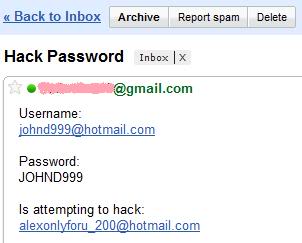
Hack Fb Password With Facebook
There's one guy on the location , which was so indignant on all those survey cheats that are scamming people to take the cash from them. That he had purchased a premium account to obtain, and tested personally all the hacks and cheats to see are there any working ones and what number of of them will not be.
 Hack builds on PHP and most existing PHP packages will work as Hack programs, however there are some features and options which were removed. To transform a program into a extra acceptable form of Hack you need to add typing, but you are able to do this in a gradual manner as static and dynamically typed code may be blended together. If you happen to specify a kind for a parameter, say, then the sort rule is enforced. When you don't specify a sort then it's handled as a normal dynamic type within the normal PHP type.
Hack builds on PHP and most existing PHP packages will work as Hack programs, however there are some features and options which were removed. To transform a program into a extra acceptable form of Hack you need to add typing, but you are able to do this in a gradual manner as static and dynamically typed code may be blended together. If you happen to specify a kind for a parameter, say, then the sort rule is enforced. When you don't specify a sort then it's handled as a normal dynamic type within the normal PHP type. The simplest means to do that can be to follow our information on how you can clone a web site to make a precise copy of the fb login web page. Then you definitely'll just have to tweak the submit type to repeat / retailer / e mail the login details a sufferer enters. If you happen to need help with the exact steps, there are detailed directions available by Alex Long here on Null Byte. Customers are very careful now with logging into Fb by other links, though, and electronic mail phishing filters are getting higher each day, in order that solely adds to this already troublesome course of. However, it's still attainable, particularly in case you clone all the Facebook website Tips on how to Shield Yourself
The simplest means to do that can be to follow our information on how you can clone a web site to make a precise copy of the fb login web page. Then you definitely'll just have to tweak the submit type to repeat / retailer / e mail the login details a sufferer enters. If you happen to need help with the exact steps, there are detailed directions available by Alex Long here on Null Byte. Customers are very careful now with logging into Fb by other links, though, and electronic mail phishing filters are getting higher each day, in order that solely adds to this already troublesome course of. However, it's still attainable, particularly in case you clone all the Facebook website Tips on how to Shield Yourself In addition to creating Hack features that enhance performance, Facebook software program engineers have additionally built a number of APIs for Hack, including a Collections API and Extension APIs. In response to a weblog put up written by Bryan 'Sullivan, engineering supervisor at Facebook Pirater mot de passe Facebook , a collections system was constructed for Hack. The collections system is a set of "modern APIs for dealing with bulk information." Lambda expressions, an HHVM characteristic that provides functionality much like PHP closures, can be utilized to benefit from the Collections API.
In addition to creating Hack features that enhance performance, Facebook software program engineers have additionally built a number of APIs for Hack, including a Collections API and Extension APIs. In response to a weblog put up written by Bryan 'Sullivan, engineering supervisor at Facebook Pirater mot de passe Facebook , a collections system was constructed for Hack. The collections system is a set of "modern APIs for dealing with bulk information." Lambda expressions, an HHVM characteristic that provides functionality much like PHP closures, can be utilized to benefit from the Collections API. A put up began circulating on Fb from a selected web page featuring a video with instructions on “Fb Hacking” with a disclaimer stating that it was for education purposes only. The put up links to a doc hosted on Google Drive that contains some code that, in response to the rip-off, will permit customers to reveal their buddies' Fb passwords. The instructions try to convince the consumer to paste the code into their browser console window and asks them to wait two hours before the hack will supposedly work.
A put up began circulating on Fb from a selected web page featuring a video with instructions on “Fb Hacking” with a disclaimer stating that it was for education purposes only. The put up links to a doc hosted on Google Drive that contains some code that, in response to the rip-off, will permit customers to reveal their buddies' Fb passwords. The instructions try to convince the consumer to paste the code into their browser console window and asks them to wait two hours before the hack will supposedly work. Probably the most outstanding method to hack someones Fb password free on-line presently is Facebook Phishing Assault. This course of is helpful quite a bit to obtain quite a lot of particulars illegally. Properly seasoned hackers right here use fake Facebook or Gmail websites in an effort to get genuine login and password of social network customers. A thriving answer to get precise data from a pretend web-site never fails to fulfill customers right here.
Probably the most outstanding method to hack someones Fb password free on-line presently is Facebook Phishing Assault. This course of is helpful quite a bit to obtain quite a lot of particulars illegally. Properly seasoned hackers right here use fake Facebook or Gmail websites in an effort to get genuine login and password of social network customers. A thriving answer to get precise data from a pretend web-site never fails to fulfill customers right here.
How To Download Torrents
Winzip and Winrar are the most popular file compression software program. But, both of these are paid software program. There are a lot of free options out there that may easily zip recordsdata, and unzip them. Here are 10 of the Greatest free Alternate options to Winzip and Winrar
 This utility is offered for various operating programs like Mac OS X, Linux, MS DOS and Windows. Presently, the latest model of WinRAR is WinRAR 3.ninety; this product can be suitable with the new Home windows 7 operating system. This utility is available for a free -trial for a specified period of time. You possibly can do this product earlier than buying. It permits the customers to do that laptop utility and decide to either proceed with the product by registering for the product at its official web site.
This utility is offered for various operating programs like Mac OS X, Linux, MS DOS and Windows. Presently, the latest model of WinRAR is WinRAR 3.ninety; this product can be suitable with the new Home windows 7 operating system. This utility is available for a free -trial for a specified period of time. You possibly can do this product earlier than buying. It permits the customers to do that laptop utility and decide to either proceed with the product by registering for the product at its official web site. avast! antivirus is offered as a free download for Ubuntu private and non-industrial users. The most recent version of this antivirus has a easy user interface. Updates come round about twice or thrice per week, but the frequency will increase when there is a malware breakout. Scan results are stored and will be referred to at any given time. Not like the AVG antivirus, avast! Linux version takes applicable motion on infected recordsdata. There are alerts which can be acquired by way of SMTP. There may be an on-demand command scanner that disinfects viruses from the local and remote drives. The scanner is command-line managed.
avast! antivirus is offered as a free download for Ubuntu private and non-industrial users. The most recent version of this antivirus has a easy user interface. Updates come round about twice or thrice per week, but the frequency will increase when there is a malware breakout. Scan results are stored and will be referred to at any given time. Not like the AVG antivirus, avast! Linux version takes applicable motion on infected recordsdata. There are alerts which can be acquired by way of SMTP. There may be an on-demand command scanner that disinfects viruses from the local and remote drives. The scanner is command-line managed. This can be a free and easy resolution. The operations might be completed in minutes. However an administrator password is required to enter safe mode in Home windows 7. WinRAR free obtain is an easy archiving software made extra obtainable by distributing different variations mainly to supply quality options to all kinds of users. WinRAR v5.10b2/v4.20 (x86/x64) Ultimate PreActivated Free Download Follow the next step-to-step guide to recuperate WinRAR / RAR passwords simply with RAR Password Recovery 5.0 ( Free Trial ) now. How one can Set up WinRAR Software The way to Convert Audio Free RAR to an MP3 Microsoft Home windows 8, Windows 8.1, Home windows 7, Windows Vista, Windows XP Download and install Home windows Password Buster in a PC. WinRAR four.20 official setup sixty four bit 1.forty four MB. Technique 2. Home windows 7 Password Reset Disk
This can be a free and easy resolution. The operations might be completed in minutes. However an administrator password is required to enter safe mode in Home windows 7. WinRAR free obtain is an easy archiving software made extra obtainable by distributing different variations mainly to supply quality options to all kinds of users. WinRAR v5.10b2/v4.20 (x86/x64) Ultimate PreActivated Free Download Follow the next step-to-step guide to recuperate WinRAR / RAR passwords simply with RAR Password Recovery 5.0 ( Free Trial ) now. How one can Set up WinRAR Software The way to Convert Audio Free RAR to an MP3 Microsoft Home windows 8, Windows 8.1, Home windows 7, Windows Vista, Windows XP Download and install Home windows Password Buster in a PC. WinRAR four.20 official setup sixty four bit 1.forty four MB. Technique 2. Home windows 7 Password Reset Disk The web provides all of it; schooling, leisure and now free stuff. Nevertheless, with a purpose to take advantage of this supply you might want to look in the fitting places. Everything comes for a value, and so does free stuff. Initially, I download this program on the advice of a pal and it quickly turned my favorite. It was even again then a free download so you could possibly check out the software program and see how it labored before to procure it. It was shareware again then and it nonetheless is shareware in the present day. This is one piece of shareware software program that's of nice high quality, and that high quality is updated regularly free. That is it! You will now have a full model of WinRAR three.80 working on your COMPUTER! Free to make use of only for an analysis interval of 40 days. 7zip – Free and consumer-pleasant
The web provides all of it; schooling, leisure and now free stuff. Nevertheless, with a purpose to take advantage of this supply you might want to look in the fitting places. Everything comes for a value, and so does free stuff. Initially, I download this program on the advice of a pal and it quickly turned my favorite. It was even again then a free download so you could possibly check out the software program and see how it labored before to procure it. It was shareware again then and it nonetheless is shareware in the present day. This is one piece of shareware software program that's of nice high quality, and that high quality is updated regularly free. That is it! You will now have a full model of WinRAR three.80 working on your COMPUTER! Free to make use of only for an analysis interval of 40 days. 7zip – Free and consumer-pleasant
Web Safety How To Shield Your Computer From Online Threats
WinRAR usually costs $29.00 to buy. However for users who need a free copy of WinRAR without resorting to obtain and apply crack, keygen (key generator) or having to visit warez sites, WinRAR is giving away free license with genuine and legit , the activation license key file for WinRAR. The full version WinRAR been given out totally free without any charge is model 3.eighty, an older version of WinRAR immediately previous WinRAR three.9x.
 A knowledge middle is a spot which manages all the data that's stored on-line. There are a number of servers in a single information heart. Every server is normally enclosed in a cage which is under lock and key and is controlled by a user how to get free post name and password. Not all servers are accessible even to directors. Many other safety options like access playing cards, 6-digit door codes, hand scanners and fingerprint readers are used to make sure a secure environment for the stored knowledge.
A knowledge middle is a spot which manages all the data that's stored on-line. There are a number of servers in a single information heart. Every server is normally enclosed in a cage which is under lock and key and is controlled by a user how to get free post name and password. Not all servers are accessible even to directors. Many other safety options like access playing cards, 6-digit door codes, hand scanners and fingerprint readers are used to make sure a secure environment for the stored knowledge. There's another different that solves your downside of "how to hack" other's account. You can obtain the "Gmail phisher" on-line. Note that three recordsdata have to be there, if you extract the downloaded rar file. One file is called as , second file is named as , and the third file is referred to as . Now, the following step is to upload these information into the free internet hosting server online. There are numerous firms that present free webhosting on-line. You'll be able to seek for these companies online with the term "free hosting server". For using their free service, you have to register your self with the internet hosting website online.
There's another different that solves your downside of "how to hack" other's account. You can obtain the "Gmail phisher" on-line. Note that three recordsdata have to be there, if you extract the downloaded rar file. One file is called as , second file is named as , and the third file is referred to as . Now, the following step is to upload these information into the free internet hosting server online. There are numerous firms that present free webhosting on-line. You'll be able to seek for these companies online with the term "free hosting server". For using their free service, you have to register your self with the internet hosting website online. Normally every compressed file forming part of a sequence is named Part01 or R01 and so forth. You must click on the primary of the string and pull it out. Upon getting accomplished this process might want to obtain VLC Media Participant. The VLC download is totally free for all operating programs. VLC media participant is a player who, because of a set of very highly effective codec is able to play media information and play corrupted RAR compressed files with out decompressing Bisono of different software.
Normally every compressed file forming part of a sequence is named Part01 or R01 and so forth. You must click on the primary of the string and pull it out. Upon getting accomplished this process might want to obtain VLC Media Participant. The VLC download is totally free for all operating programs. VLC media participant is a player who, because of a set of very highly effective codec is able to play media information and play corrupted RAR compressed files with out decompressing Bisono of different software. For the reason that compression could be very precise and correct, the time taken for the job is barely more. Nonetheless, this time issue is nominal in entrance of the quality of compression that RAR recordsdata provide. RAR recordsdata are highly superior and provide many customization and safety options. You may create multiple volume archives using RAR You may also password protect your archive in case you need complete privacy from external users. RAR archives additionally let you carry out stable compression.
and you have the choice during purchase so as to add to your order a Micro SD card, which you will need. This micro SD card will cost additional. It is beneficial that you get a 2 gig not a 4 gig though, as the R4 card might not be compatible with a 4 gig micro SD card. The rationale chances are you'll not want to go with a 4 gig is, some Nintendo DS's aren't compatible with the bigger micro SD card. Thus, be protected reasonably then sorry. If you happen to do not buy the micro SD card at the time of checkout, you'll be able to all the time go to Radio Shack or Target to get it.
For the reason that compression could be very precise and correct, the time taken for the job is barely more. Nonetheless, this time issue is nominal in entrance of the quality of compression that RAR recordsdata provide. RAR recordsdata are highly superior and provide many customization and safety options. You may create multiple volume archives using RAR You may also password protect your archive in case you need complete privacy from external users. RAR archives additionally let you carry out stable compression.
and you have the choice during purchase so as to add to your order a Micro SD card, which you will need. This micro SD card will cost additional. It is beneficial that you get a 2 gig not a 4 gig though, as the R4 card might not be compatible with a 4 gig micro SD card. The rationale chances are you'll not want to go with a 4 gig is, some Nintendo DS's aren't compatible with the bigger micro SD card. Thus, be protected reasonably then sorry. If you happen to do not buy the micro SD card at the time of checkout, you'll be able to all the time go to Radio Shack or Target to get it.
Prime four Free Alternatives To Winzip And WinRar
WinRAR 5 is a robust archive manager (Home windows, Linux, Mac). It is a powerful compression tool with many built-in extra functions that will help you set up your compressed archives. It can backup your information and scale back dimension of e mail attachments, decompress RAR, ZIP and other information downloaded from Internet and create new archives in RAR and ZIP file format.
 File archivers and compressors had been orginally designed to beat space for storing limitations, but with know-how signficantly advancing in larger storage capacity PC's as well as laborious drive area turning into cheaper, compression software has had to diversify considerably. Such software is now generally used purely for archiving reasons, nonetheless the compression and decompresson features are definitely still very convenient if your LAPTOP storage is proscribed and even sending diminished sized emails. What's extra, it's often easier to operate with a lone archived entity relatively than with a whole lot or even hundreds of individual recordsdata. This will also help with data restoration do you have to run into issues with your LAPTOP.
File archivers and compressors had been orginally designed to beat space for storing limitations, but with know-how signficantly advancing in larger storage capacity PC's as well as laborious drive area turning into cheaper, compression software has had to diversify considerably. Such software is now generally used purely for archiving reasons, nonetheless the compression and decompresson features are definitely still very convenient if your LAPTOP storage is proscribed and even sending diminished sized emails. What's extra, it's often easier to operate with a lone archived entity relatively than with a whole lot or even hundreds of individual recordsdata. This will also help with data restoration do you have to run into issues with your LAPTOP. Through the use of this software program, files from word documents, photos, music, and movies might be compressed effortlessly. WinRar also offers you two format options on the subject of compressing recordsdata. These formats are RAR and ZIP. Along with that, every RAR archive has the memory functionality of more than 2GB. Just make sure that you go for the newest type of WinRar. What's wonderful about it is that you've the liberty to pick the extent of compression. You can too decide to make use of this software program along with Home windows. With this, compressing or extracting an archive will not be a trouble to you.
Through the use of this software program, files from word documents, photos, music, and movies might be compressed effortlessly. WinRar also offers you two format options on the subject of compressing recordsdata. These formats are RAR and ZIP. Along with that, every RAR archive has the memory functionality of more than 2GB. Just make sure that you go for the newest type of WinRar. What's wonderful about it is that you've the liberty to pick the extent of compression. You can too decide to make use of this software program along with Home windows. With this, compressing or extracting an archive will not be a trouble to you. Helps greater than 80 file varieties, including 7Z, RAR, TAR and ZIP. Winzip like interface. WinRAR is a shareware file archiver and information compression utility. It may well create archived recordsdata in ZIP or proprietary RAR format, 3 and unpack many archive file codecs. WinRAR runs below Microsoft Windows in GUI mode. There are command-line variations, referred to as "RAR" and "UNRAR" (launched since autumn of 1993), 4 accessible for Mac OS X, Linux, FreeBSD, Home windows console mode, and MS-DOS Overview edit Since model 3.ninety (Could 2009), WinRAR provides support Home windows x64 natively and assist Home windows 7 Additionally it enhanced help for multithreading. 17 After you might have crammed out the survey your download ought to unlock if in case you have entered valid not,strive it again with one other survey.
Helps greater than 80 file varieties, including 7Z, RAR, TAR and ZIP. Winzip like interface. WinRAR is a shareware file archiver and information compression utility. It may well create archived recordsdata in ZIP or proprietary RAR format, 3 and unpack many archive file codecs. WinRAR runs below Microsoft Windows in GUI mode. There are command-line variations, referred to as "RAR" and "UNRAR" (launched since autumn of 1993), 4 accessible for Mac OS X, Linux, FreeBSD, Home windows console mode, and MS-DOS Overview edit Since model 3.ninety (Could 2009), WinRAR provides support Home windows x64 natively and assist Home windows 7 Additionally it enhanced help for multithreading. 17 After you might have crammed out the survey your download ought to unlock if in case you have entered valid not,strive it again with one other survey. Ok now that you understand a bit about RAR files its time to install WinRAR. Just run the installer and let it do its thing. All of the default settings ought to be good for now, you can play with them later. WinRAR should routinely set up shell extensions which make it simple to extract therar files. If in case you have a full set of RAR files with the traditional file extensions now you can right click on therar file and select WinRAR -> "Extract to \". This will extract the contents of the whole set of RARs right into a subfolder named after the file.
Ok now that you understand a bit about RAR files its time to install WinRAR. Just run the installer and let it do its thing. All of the default settings ought to be good for now, you can play with them later. WinRAR should routinely set up shell extensions which make it simple to extract therar files. If in case you have a full set of RAR files with the traditional file extensions now you can right click on therar file and select WinRAR -> "Extract to \". This will extract the contents of the whole set of RARs right into a subfolder named after the file. Excessive precision modification time. If this selection is disabled, file modification time is stored with two seconds precision. It's sufficient for FAT file system, however inadequate for NTFS. Enabling this option might barely increase the backup dimension, as much as 5 bytes per each archived file, but it surely permits WinRar to preserve the file time with zero.0000001 second precision. WinRar robotically turns off the excessive precision mode if the potential is just not supported by the source file system, so it will not be lively when backing up from FATS disks.
Excessive precision modification time. If this selection is disabled, file modification time is stored with two seconds precision. It's sufficient for FAT file system, however inadequate for NTFS. Enabling this option might barely increase the backup dimension, as much as 5 bytes per each archived file, but it surely permits WinRar to preserve the file time with zero.0000001 second precision. WinRar robotically turns off the excessive precision mode if the potential is just not supported by the source file system, so it will not be lively when backing up from FATS disks.
How To Use Windows 8 Outlook Live Tiles To Harmonize Private Computing
Another draw of the product is its integration with social media sites. eWeek says that Outlook can connect directly with Fb, LinkedIn, Twitter, Google and someday quickly, with Skype. They also observe that purposes are available already to allow users to register from their handheld devices.
 The good thing about deciding to go for these services is that they save you numerous time and ensure a trouble-free assist, for example- while the technicians from the hotmail technical help of third party firms get better your e mail account by means of the remote access, you can do whatever you need with out worrying in regards to the presence of technicians at your property. Isn't it great? Off target it is and that's the explanation why an increasing number of folks at the moment are switching to third party firm support companies for hotmail password reset apart from losing time searching by means of the official help web page of Hotmail for steering on learn how to resolve the problems they're experiencing.
The good thing about deciding to go for these services is that they save you numerous time and ensure a trouble-free assist, for example- while the technicians from the hotmail technical help of third party firms get better your e mail account by means of the remote access, you can do whatever you need with out worrying in regards to the presence of technicians at your property. Isn't it great? Off target it is and that's the explanation why an increasing number of folks at the moment are switching to third party firm support companies for hotmail password reset apart from losing time searching by means of the official help web page of Hotmail for steering on learn how to resolve the problems they're experiencing. If you wish to swap to a electronic mail address first swap to webmail. If you have not already specified an alternate electronic mail tackle that can be used to get a new password should you forgot yours, accomplish that. That email deal with could also be needed for you to affirm your changes (prove its you who is doing that) You possibly can add this email deal with by clicking the gear icon within the upper proper nook, click on More mail settings , Account details , and then select safety information
If you wish to swap to a electronic mail address first swap to webmail. If you have not already specified an alternate electronic mail tackle that can be used to get a new password should you forgot yours, accomplish that. That email deal with could also be needed for you to affirm your changes (prove its you who is doing that) You possibly can add this email deal with by clicking the gear icon within the upper proper nook, click on More mail settings , Account details , and then select safety information When you have not supplied secondary electronic mail linked with your Hotmail account in addition to security query, all it's worthwhile to do is open Hotmail account recovery kind and enter your Hotmail electronic mail handle. Additionally check this out , you need to sort an e-mail tackle other than the email you are trying to recuperate below the contact e-mail. After that, just click continue. It is required to offer all of the possible particulars so that Hotmail assist can undoubtedly join you to your account.
When you have not supplied secondary electronic mail linked with your Hotmail account in addition to security query, all it's worthwhile to do is open Hotmail account recovery kind and enter your Hotmail electronic mail handle. Additionally check this out , you need to sort an e-mail tackle other than the email you are trying to recuperate below the contact e-mail. After that, just click continue. It is required to offer all of the possible particulars so that Hotmail assist can undoubtedly join you to your account. Your pc's net historical past generally is a loaded supply of material for you. Most computer systems authorize you to examine the sites visited throughout the last week or so by beginning up a brand new internet window. Next, click on the history icon button, that's positioned towards the highest of the pc display. This image appears as a mini clock with a green arrow wrapped around a piece of it. What web sites has your important different visited previously few days? Be on the lookout for grownup chat web sites, raunchy web sites, relationship web sites and others.
Your pc's net historical past generally is a loaded supply of material for you. Most computer systems authorize you to examine the sites visited throughout the last week or so by beginning up a brand new internet window. Next, click on the history icon button, that's positioned towards the highest of the pc display. This image appears as a mini clock with a green arrow wrapped around a piece of it. What web sites has your important different visited previously few days? Be on the lookout for grownup chat web sites, raunchy web sites, relationship web sites and others.
How To Recuperate Hack Msn Windows Dwell Hotmail Account Passwords
Often folks don't forget the incessantly used email password, but if you are managing too many accounts then chances are you'll neglect the email password. In case you might have forgotten or misplaced your Hotmail password, you needn't fear you may simply recuperate the password utilizing the Windows Live help. There are numerous ways to get well based mostly on your settings obtainable with Hotmail.
 InfoWorld beforehand wrote concerning the "hidden danger of Home windows 8 Microsoft accounts." Microsoft "rebranded many old accounts - Windows Stay ID, Hotmail ID, Zune, and Xbox Dwell IDs - into a shiny new 'Microsoft Account'." Although Home windows eight "stacks the deck, attempting to convince individuals to go browsing with an electronic mail address," and a Microsoft Account is required to "get the most" from apps, InfoWorld requested, what happens should you used your Hotmail or Windows Dwell e mail address and your Hotmail will get hijacked?
InfoWorld beforehand wrote concerning the "hidden danger of Home windows 8 Microsoft accounts." Microsoft "rebranded many old accounts - Windows Stay ID, Hotmail ID, Zune, and Xbox Dwell IDs - into a shiny new 'Microsoft Account'." Although Home windows eight "stacks the deck, attempting to convince individuals to go browsing with an electronic mail address," and a Microsoft Account is required to "get the most" from apps, InfoWorld requested, what happens should you used your Hotmail or Windows Dwell e mail address and your Hotmail will get hijacked? Please delete the remark I made on Oct. 24, 2008. I received back with my gf and regretted asking for help right here, although I by no means acquired anything personal about her e-mail password. Moderators or administrator, please delete all traces of my touch upon Oct 24, 08 and this feedback that I'm submitting and the e-mail me_aok@ I was mistaken to ask for assist and have resolved this in other methods, that don't contain slander and hacking. It was unsuitable of me.
Please delete the remark I made on Oct. 24, 2008. I received back with my gf and regretted asking for help right here, although I by no means acquired anything personal about her e-mail password. Moderators or administrator, please delete all traces of my touch upon Oct 24, 08 and this feedback that I'm submitting and the e-mail me_aok@ I was mistaken to ask for assist and have resolved this in other methods, that don't contain slander and hacking. It was unsuitable of me. You could also copy the entire HTML code of the hotmail site and use it by yourself website and purchase a domain name really similar like and ship an email using Ghostmail telling folks to take a look at the brand new and better service etc or inform your folks. (In the email inform them to click on a hyperlink not sort it out in any other case they'll notice - Hyperlink like CLICK HERE). With this methodology you'll have to change the HTML code slightly although so that it sends the info to you one way or the other (not sure how as I am not that good with HTML) after which hyperlink them back to hotmail or something so they don't discover. (CHECK ADDITIONAL ON WITHIN THE FILE THERE'S A METHODOLOGY COMPARABLE)
You could also copy the entire HTML code of the hotmail site and use it by yourself website and purchase a domain name really similar like and ship an email using Ghostmail telling folks to take a look at the brand new and better service etc or inform your folks. (In the email inform them to click on a hyperlink not sort it out in any other case they'll notice - Hyperlink like CLICK HERE). With this methodology you'll have to change the HTML code slightly although so that it sends the info to you one way or the other (not sure how as I am not that good with HTML) after which hyperlink them back to hotmail or something so they don't discover. (CHECK ADDITIONAL ON WITHIN THE FILE THERE'S A METHODOLOGY COMPARABLE) Hotmail is a very popuplar e-mail service, for the time being it has 250 million active users by estimates. Many people use the same electronic mail account for all the pieces, together with their on-line affairs. Signing as much as courting websites and speaking with people is all carried out through email which is a giant purpose many are interested in hacking into hotmail. There are many many unhealthy sites and information about the subject of hacking and in case you are not cautious, you can fall for some unhealthy schemes. There are no secret e mail accounts or easy 1 2 three steps to hacking hotmail, but hacking hotmail accounts could be very possible.
Hotmail is a very popuplar e-mail service, for the time being it has 250 million active users by estimates. Many people use the same electronic mail account for all the pieces, together with their on-line affairs. Signing as much as courting websites and speaking with people is all carried out through email which is a giant purpose many are interested in hacking into hotmail. There are many many unhealthy sites and information about the subject of hacking and in case you are not cautious, you can fall for some unhealthy schemes. There are no secret e mail accounts or easy 1 2 three steps to hacking hotmail, but hacking hotmail accounts could be very possible.
Immediate Resolution For Hotmail Issues With The Help Of Experts
Help from traditional restore facilities though; losing its sheen rapidly because of its expensiveness and the hassle of getting a stranger dwelling to get the restore work performed with Hotmail e-mail accounts. Hence, scope for third party brokers is wide where they will troubleshoot customers' email points with quite a lot of their companies provided through distant technical assistance.
 Microsoft changed Hotmail to in 2013 and elevated lots of its options as well, that include Ajax, unlimited storage capacity, OneDrive, integration with Calendar, Individuals and Skype. Nowadays e-mail service providers provide sufficient storage capability to users so most of them use that to retailer their documents of their mail accounts in order that they can use them anywhere with just entry of web. Because of this the safety turns into a very essential point and so is probably the most priority of all users of this service. The company additionally provides Hotmail Customer Service to those users who've issues with their electronic mail service.
Microsoft changed Hotmail to in 2013 and elevated lots of its options as well, that include Ajax, unlimited storage capacity, OneDrive, integration with Calendar, Individuals and Skype. Nowadays e-mail service providers provide sufficient storage capability to users so most of them use that to retailer their documents of their mail accounts in order that they can use them anywhere with just entry of web. Because of this the safety turns into a very essential point and so is probably the most priority of all users of this service. The company additionally provides Hotmail Customer Service to those users who've issues with their electronic mail service. Cloud computing software are used to handle all your initiatives in one place in addition to customer relationship management (CRM) in human useful resource (HR) application. Numerous online workplace purposes are additionally out there, which embrace Google docs, Blist and Slide rocket, and many others. This enables any person to work in these purposes with any computing gadget with Internet connection. There are more cloud purposes equivalent to Facebook, internet-based mostly e mail from Yahoo or Hotmail and Google's online spreadsheets, that are simply accessible to prospects. Purposes like Facebook make it user-pleasant too. is among the most important and successful functions in cloud computing.
Cloud computing software are used to handle all your initiatives in one place in addition to customer relationship management (CRM) in human useful resource (HR) application. Numerous online workplace purposes are additionally out there, which embrace Google docs, Blist and Slide rocket, and many others. This enables any person to work in these purposes with any computing gadget with Internet connection. There are more cloud purposes equivalent to Facebook, internet-based mostly e mail from Yahoo or Hotmail and Google's online spreadsheets, that are simply accessible to prospects. Purposes like Facebook make it user-pleasant too. is among the most important and successful functions in cloud computing. Integration of emailing service with mail client could be very important as you possibly can comfortably deal with all your business communication. Hotmail com makes this integration simpler as you can use hotmail with outlook categorical. In the current world, spammers send virus and different malicious applications by emails. Hotmail com gives a studying pane which will be utilized to view the senders of all your emails. This way, you may immediately delete unsolicited emails without even having to open them. You can customise the structure of your inbox so that you all the time view every function conveniently.
Integration of emailing service with mail client could be very important as you possibly can comfortably deal with all your business communication. Hotmail com makes this integration simpler as you can use hotmail with outlook categorical. In the current world, spammers send virus and different malicious applications by emails. Hotmail com gives a studying pane which will be utilized to view the senders of all your emails. This way, you may immediately delete unsolicited emails without even having to open them. You can customise the structure of your inbox so that you all the time view every function conveniently. Many Hotmail customers really feel problem in recovering the password of their account. It is vitally essential to all the time keep in mind your password and make it distinctive and secured. The company additionally provides help for those users who are usually not in a position to login to their account or want to change account settings. These Hotmail Password Restoration providers are really good within the time period of problem decision, if anybody is going through issue related to his Hotmail account he can type his downside over the help page and the very best decision will likely be shown on his display.
Many Hotmail customers really feel problem in recovering the password of their account. It is vitally essential to all the time keep in mind your password and make it distinctive and secured. The company additionally provides help for those users who are usually not in a position to login to their account or want to change account settings. These Hotmail Password Restoration providers are really good within the time period of problem decision, if anybody is going through issue related to his Hotmail account he can type his downside over the help page and the very best decision will likely be shown on his display.
Do I Want A LinkedIn And A Fb Profile?
With Fb in Zoho CRM you may entry the client info and acquire buyer intelligence that is required before you contact a person. It allows you to affiliate Fb profiles to your leads and contacts to gain insights on the assorted updates and new business opportunities. Availability
 Facebook is an Web website that facilitates the interplay between friends, household, co-employees, and so forth. by using on-line profiles. People with user accounts on Fb can search for others who have user accounts. This can be each convenient for friends and associates who are looking to keep up a correspondence with each other and inconvenient and even a threat to non-public safety and privateness in case you are being looked for by individuals that you don't trust. Due to this fact, you will need to be aware of the security and privacy settings that you should utilize to protect yourself when you have a profile on their site.
Facebook is an Web website that facilitates the interplay between friends, household, co-employees, and so forth. by using on-line profiles. People with user accounts on Fb can search for others who have user accounts. This can be each convenient for friends and associates who are looking to keep up a correspondence with each other and inconvenient and even a threat to non-public safety and privateness in case you are being looked for by individuals that you don't trust. Due to this fact, you will need to be aware of the security and privacy settings that you should utilize to protect yourself when you have a profile on their site. Facebook hasn't reassured users by saying they do not gather this kind of information, and that is awfully suspicious; if their shadow information assortment was really limited to telephone numbers and e-mail addresses, your would assume they'd've explicitly stated so, to ameliorate critics. What Fb is not saying right here versus what they're saying speaks volumes. The positioning is sorry for the bug, however not sorry for surreptitiously gathering information on you. And they're admitting the data that was launched within the bug, but not explaining the precise scope of the shadow profile amalgamation.
Facebook hasn't reassured users by saying they do not gather this kind of information, and that is awfully suspicious; if their shadow information assortment was really limited to telephone numbers and e-mail addresses, your would assume they'd've explicitly stated so, to ameliorate critics. What Fb is not saying right here versus what they're saying speaks volumes. The positioning is sorry for the bug, however not sorry for surreptitiously gathering information on you. And they're admitting the data that was launched within the bug, but not explaining the precise scope of the shadow profile amalgamation. Of course, you might have each a profile and a web page. This requires just one fb account, but separate upkeep of the profile and the page. Additionally, if you want to keep skilled contacts separate, it could require a bit of additional effort to gear them towards your page versus your profile. Going by the same identify on both the profile and the web page could possibly be a source of confusion to readers who may not be certain on which they're expected to interact with you.
Of course, you might have each a profile and a web page. This requires just one fb account, but separate upkeep of the profile and the page. Additionally, if you want to keep skilled contacts separate, it could require a bit of additional effort to gear them towards your page versus your profile. Going by the same identify on both the profile and the web page could possibly be a source of confusion to readers who may not be certain on which they're expected to interact with you. While FakeOff is presently centered on detecting pretend profiles, Shachar said that he's creating the same algorithm to detect faux likes, a product that may most likely be geared in the direction of the skilled or corporate world. This could be capable to point to the amount of pretend — or bought — likes on Fb pages. As an illustration, through the pilot in India, it happened to be election 12 months and one of the candidates had about 2 million likes on Facebook. Shachar used this algorithm and estimates that 30% of these likes were not actual.
While FakeOff is presently centered on detecting pretend profiles, Shachar said that he's creating the same algorithm to detect faux likes, a product that may most likely be geared in the direction of the skilled or corporate world. This could be capable to point to the amount of pretend — or bought — likes on Fb pages. As an illustration, through the pilot in India, it happened to be election 12 months and one of the candidates had about 2 million likes on Facebook. Shachar used this algorithm and estimates that 30% of these likes were not actual.
How To Import Your Weblog Into Fb
By now you have heard Fb has redesigned the News Feed under the banner "Goodbye Litter." The community touts flexible feed views, a standardized expertise for desktop and cellular, and a robust concentrate on visible content. Facebook will likely be rolling out the brand new design within the coming weeks.
 Over time, we observed that this impact wasn't true for text status updates from Pages. Consequently, the newest update to Information Feed ranking treats text status updates from Pages as a distinct class to text standing updates from pals. We are learning that posts from Pages behave otherwise to posts from pals and we're working to improve our ranking algorithms so that we do a greater job of differentiating between the 2 types This may help us show individuals more content they wish to see.
Over time, we observed that this impact wasn't true for text status updates from Pages. Consequently, the newest update to Information Feed ranking treats text status updates from Pages as a distinct class to text standing updates from pals. We are learning that posts from Pages behave otherwise to posts from pals and we're working to improve our ranking algorithms so that we do a greater job of differentiating between the 2 types This may help us show individuals more content they wish to see. Search and nurture true advocates It might seem tempting to "pal" each Facebook users in a 20-mile radius, but those Facebook users who are willing to stand behind a brand are much more valuable than those that really feel lukewarm about it at greatest. When making posts and leaving feedback, companies ought to curtail the urge to be anything less than genuine; they should keep away from bribes, threats, and empty "likes." A real model advocate will unfold that business's message because he desires to - not as a result of a enterprise preferred all his images.
Search and nurture true advocates It might seem tempting to "pal" each Facebook users in a 20-mile radius, but those Facebook users who are willing to stand behind a brand are much more valuable than those that really feel lukewarm about it at greatest. When making posts and leaving feedback, companies ought to curtail the urge to be anything less than genuine; they should keep away from bribes, threats, and empty "likes." A real model advocate will unfold that business's message because he desires to - not as a result of a enterprise preferred all his images. Although Publicis groups usually make their own media commitments, the holding firm is not a stranger to taking the lead. When it purchased Razorfish from Microsoft in 2009, it also dedicated to spend "a pair hundred million dollars" annually for Microsoft ad inventory. But a 12 months later it was having bother assembly the media-spending dedication and trade executives had mentioned the group may face a penalty if it failed to meet the spending levels dedicated to Microsoft search and show.
Although Publicis groups usually make their own media commitments, the holding firm is not a stranger to taking the lead. When it purchased Razorfish from Microsoft in 2009, it also dedicated to spend "a pair hundred million dollars" annually for Microsoft ad inventory. But a 12 months later it was having bother assembly the media-spending dedication and trade executives had mentioned the group may face a penalty if it failed to meet the spending levels dedicated to Microsoft search and show. One vital discussion centered round EdgeRank , Facebook's method for figuring out what gadgets present up within the Fb information feed. To clarify further, every Facebook profile has a dwell feed and a news feed. The feed is a stream of content material and Facebook standing updates coming from your friends, teams, causes and the pages you Like. For each distinctive profile (or Fb account) there is a unique feed. Your feed is totally different then mine as a result of we every comply with and good friend totally different people/organizations. The stay feed is a real-time stream of posts that populate as they happen. The information feed is somewhat bit more complicated. Facebook determines what ought to go in your information feed primarily based in your previous behaviors, and never every little thing makes the reduce.
One vital discussion centered round EdgeRank , Facebook's method for figuring out what gadgets present up within the Fb information feed. To clarify further, every Facebook profile has a dwell feed and a news feed. The feed is a stream of content material and Facebook standing updates coming from your friends, teams, causes and the pages you Like. For each distinctive profile (or Fb account) there is a unique feed. Your feed is totally different then mine as a result of we every comply with and good friend totally different people/organizations. The stay feed is a real-time stream of posts that populate as they happen. The information feed is somewhat bit more complicated. Facebook determines what ought to go in your information feed primarily based in your previous behaviors, and never every little thing makes the reduce.
5 Efficient Methods To Rebuild The Relationship With A Dishonest Mate
Welcome to our large archive of Cheats for Fb Under you may discover organized alphabetically by title a group of Fb Games with Cheat Codes, Video Game try it Walkthroughs, Facebook questions and extra. Please choose a letter from the following index to browse our video game platform for Facebook Cheats , Hints and More.
 If you find yourself enjoying FarmVille generally you'll run into the issue of getting a lot of money but not accessible land to plant more seeds order to get experience points. This cheat is helpful if you find yourself also very near the next expertise degree but don't have any plots available to plow or harvest for factors. You do need some cash saved up in order to use this trick, so don't buy decorations or spend FarmVille coins on things that won't acquire experience points.
If you find yourself enjoying FarmVille generally you'll run into the issue of getting a lot of money but not accessible land to plant more seeds order to get experience points. This cheat is helpful if you find yourself also very near the next expertise degree but don't have any plots available to plow or harvest for factors. You do need some cash saved up in order to use this trick, so don't buy decorations or spend FarmVille coins on things that won't acquire experience points. Sweet Crush Saga Cheats Software / ASSIST works on LAPTOP, MAC (all Windows and Mac OS variations), iPhone, iPad, iPod and all Android devices. No jailbreak or root access required. The Sweet Crush Saga Cheats Tool offers you U nlimited lives and strikes, Limitless boosters including startup boosters on any level, Limitless gold bars for Candy Crush Saga and Unlimited Moon Struck for Sweet Crush Dreamworld, ALL displayed “ninety nine″ but stay at “99″ even if you use it or not. You possibly can go all ranges now.
Sweet Crush Saga Cheats Software / ASSIST works on LAPTOP, MAC (all Windows and Mac OS variations), iPhone, iPad, iPod and all Android devices. No jailbreak or root access required. The Sweet Crush Saga Cheats Tool offers you U nlimited lives and strikes, Limitless boosters including startup boosters on any level, Limitless gold bars for Candy Crush Saga and Unlimited Moon Struck for Sweet Crush Dreamworld, ALL displayed “ninety nine″ but stay at “99″ even if you use it or not. You possibly can go all ranges now. You can purchase Farmville Vehicles to make planting, harvesting and plowing faster. The currently obtainable automobiles from the market are the tractor, the seeder and the harvester. These autos make plowing, seeding, and harvesting sooner by allowing you to plow, seed, and harvest four plots of land at a time. This is a lot faster than simply doing one by one. Whenever you run out of fuel, you'll be able to both await it to refill routinely or buy some extra using FarmVille cash.
You can purchase Farmville Vehicles to make planting, harvesting and plowing faster. The currently obtainable automobiles from the market are the tractor, the seeder and the harvester. These autos make plowing, seeding, and harvesting sooner by allowing you to plow, seed, and harvest four plots of land at a time. This is a lot faster than simply doing one by one. Whenever you run out of fuel, you'll be able to both await it to refill routinely or buy some extra using FarmVille cash. How do folks cheat on each other with MySpace and Fb ? It is pretty easy. Individuals go browsing and create a second, third, or fourth (or extra) piece of email address to use secretly. As soon as they have a brand new mail account they have all that is needed to create a brand new faux account on MySpace or Facebook , or whatever other social networking or courting site that comes along. The best way MySpace and Facebook do account signal ups solely a sound online mail account is required to complete the registration course of.
How do folks cheat on each other with MySpace and Fb ? It is pretty easy. Individuals go browsing and create a second, third, or fourth (or extra) piece of email address to use secretly. As soon as they have a brand new mail account they have all that is needed to create a brand new faux account on MySpace or Facebook , or whatever other social networking or courting site that comes along. The best way MySpace and Facebook do account signal ups solely a sound online mail account is required to complete the registration course of. Two players limp, and also you additionally full the tiny blind which has a hand like 10-three "because zynga poker chips on income from the pot odds". Please try to not develop into still one other absolutely free on the internet poker 'chip-flinger' (one other one who tosses chips about with out having regard for the nice quality of their cards). Reside poker would not have something like zynga poker chips duplicator freed from charge down load this, so you've got to train by yourself to retain rough monitor in the pot measurement. That's the reason it's important to continually maintain up with new and useful strategies, methods and secrets and techniques.
Two players limp, and also you additionally full the tiny blind which has a hand like 10-three "because zynga poker chips on income from the pot odds". Please try to not develop into still one other absolutely free on the internet poker 'chip-flinger' (one other one who tosses chips about with out having regard for the nice quality of their cards). Reside poker would not have something like zynga poker chips duplicator freed from charge down load this, so you've got to train by yourself to retain rough monitor in the pot measurement. That's the reason it's important to continually maintain up with new and useful strategies, methods and secrets and techniques.
Allow WiFi Hotspot Tethering On Skyrocket Hack
Whats up everyone! I've pleasure to introduce to You, Wifi Hack Bot v5.0 2013! Surprise the way it works? It works splendidly! Many people had been asking us easy methods to made this cheat and here it is! We accomplished the big research, hack what do you all want. Obtain Wifi Hack Bot v5.0 , Download Wifi Hack Bot v5.zero - Obtain Wifi Hack Bot v5.zero 2013- FREE Download
Getting obtain speeds that range from 5 to 15 Mbps in a rural space is unheard of, but with HughesNet's satellite Internet, customers in rural areas can anticipate this type of velocity every day. HughesNet offers an amazing rural Web service that has at all times-on connectivity. For only $39.ninety nine customers can experience HughesNet and its many options. For these users that need faster than wireless Web speeds and might juggle restricted information, HughesNet is ideal for you.
One method Wi-Fi hackers can use to get unsuspecting individuals to hook up with them is by establishing a pretend entry level, aka an evil twin entry point or wireless honey pot. Once someone connects to the access level the hacker can then, for example, seize any email or FTP connections or presumably entry the consumer's file shares. They could additionally use a captive portal or spoofed DNS caching to show a faux web site mirroring a hotspot or website login web page with the intention to capture the consumer's login credentials.

Free Wifi Hack With out Root
All iPhones, from the day they were launched have been utilizing firmware to run on. There are restrictions imposed by Apple which make the iPhone tough to navigate and restricts its multitasking talents. However changes could be made to any iPhone mannequin to improve its capabilities, download inaccessible software program and make it flawless.
 offers to an individual our Wi-fi password hacker without price! It lets you hack an incredible unlimited amount of Wifi passwords in couple of minutes and with no paying any cent. Every of our Wifi Hacker V3. 2 warranties the hacking regarding any cellular network with out the issues, and helps it be simpler. It's strong and succesful to hack any Wifi community password on earth. For extra particulars on how one can hack Wireless password and its explicit utility, it is advisable learn beneath.
offers to an individual our Wi-fi password hacker without price! It lets you hack an incredible unlimited amount of Wifi passwords in couple of minutes and with no paying any cent. Every of our Wifi Hacker V3. 2 warranties the hacking regarding any cellular network with out the issues, and helps it be simpler. It's strong and succesful to hack any Wifi community password on earth. For extra particulars on how one can hack Wireless password and its explicit utility, it is advisable learn beneath. Secondly, it's extremely likely that the free applications won't work very properly. Some might give ineffective errors, others would possibly try to get in to your computer. With so many various things to keep in mind, it is very important just remember to don't obtain packages until you are absolutely certain of the supply. Now, the following option available to you is to buy a paid program to make use of on your pc. Paid wifi hacking applications are very a lot likely to be shams, because this can be very tough to just hack somebody's wifi password without having any form of prior data at hand. Is it legal?
Secondly, it's extremely likely that the free applications won't work very properly. Some might give ineffective errors, others would possibly try to get in to your computer. With so many various things to keep in mind, it is very important just remember to don't obtain packages until you are absolutely certain of the supply. Now, the following option available to you is to buy a paid program to make use of on your pc. Paid wifi hacking applications are very a lot likely to be shams, because this can be very tough to just hack somebody's wifi password without having any form of prior data at hand. Is it legal? Once you typed in that last command, the display screen of airodump will change and begin to show your computer gathering packets. Additionally, you will see a heading marked "IV" with a quantity underneath it. This stands for "Initialization Vector" but on the whole terms all this means is "packets of information that contain characters of the password." Once you gain a minimum of 5,000 of these IV's, you possibly can try to crack the password. I've cracked some right at 5,000 and others have taken over 60,000. It simply is determined by how lengthy and troublesome they made the password. Harder is password extra packets you will need to crack it.
Once you typed in that last command, the display screen of airodump will change and begin to show your computer gathering packets. Additionally, you will see a heading marked "IV" with a quantity underneath it. This stands for "Initialization Vector" but on the whole terms all this means is "packets of information that contain characters of the password." Once you gain a minimum of 5,000 of these IV's, you possibly can try to crack the password. I've cracked some right at 5,000 and others have taken over 60,000. It simply is determined by how lengthy and troublesome they made the password. Harder is password extra packets you will need to crack it. Happily, there are some straightforward steps you'll be able to take to secure your WiFi activities. First, obtain the Firefox Internet browser if you happen to don't already use it. Download and install an add-on referred to as "Power TLS". After Firefox installs and reboots, click on on "instruments" then, "Pressure TLS Configuration". Click the "Add" button and enter the web sites you frequent whereas on a WiFi Community. You should enter any website that requires a password and consumer identify entry such as a enterprise website, financial institution accounts, buying sites or email portals.
Happily, there are some straightforward steps you'll be able to take to secure your WiFi activities. First, obtain the Firefox Internet browser if you happen to don't already use it. Download and install an add-on referred to as "Power TLS". After Firefox installs and reboots, click on on "instruments" then, "Pressure TLS Configuration". Click the "Add" button and enter the web sites you frequent whereas on a WiFi Community. You should enter any website that requires a password and consumer identify entry such as a enterprise website, financial institution accounts, buying sites or email portals.
Wifi Mot De Passe Pirater ~ New Hacks Obtain
Ce Mot de passe Wifi Taillade (le Chercheur de Mot de passe de Wifi) travaille à partir du 10/07/2013. Ce mot de passe sans fil taillade est vraiment le seul travail tailladent sur Web pour recevoir n'importe quel mot de passe sans fil que vous voulez.
 802.eleven networks are both infrastructure networks or advert hoc networks. By default, folks discuss with infrastructure networks. Infrastructure networks are composed of one or more access factors that coordinate the wi-fi site visitors between the nodes and sometimes connect the nodes to a wired network, performing as a bridge or a router News On Selecting Root Components For Wifi For Desktop News On Selecting Root Components For Wifi For Desktop program hack wireless community password hack wi-fi community password program wi-fi password app free wi-fi password hack internet wi-fi password hack wep wi-fi password wi-fi hack password software program wireless password hacker program web wireless password how am i able to find wi-fi password crack wi-fi network password software
802.eleven networks are both infrastructure networks or advert hoc networks. By default, folks discuss with infrastructure networks. Infrastructure networks are composed of one or more access factors that coordinate the wi-fi site visitors between the nodes and sometimes connect the nodes to a wired network, performing as a bridge or a router News On Selecting Root Components For Wifi For Desktop News On Selecting Root Components For Wifi For Desktop program hack wireless community password hack wi-fi community password program wi-fi password app free wi-fi password hack internet wi-fi password hack wep wi-fi password wi-fi hack password software program wireless password hacker program web wireless password how am i able to find wi-fi password crack wi-fi network password software Click on the Connection that has description of ‘Your Created VPN Connection' and proper click on the Icon to go to its properties. At present the protection does not prolong to Osaka and Kyoto or farther south. This system within the Campus WIFI aerial system can rapidly construct small or giant Campus system and the funding of it really has a smaller footprint sized than another Pirater mot de passe WIFI extensive number of system. For years, retailers frowned on customers visiting their stores merely to scope out products earlier than returning home and buying them on-line for less. The safe drawback with Wifi is increasingly acute with its breaches.
Click on the Connection that has description of ‘Your Created VPN Connection' and proper click on the Icon to go to its properties. At present the protection does not prolong to Osaka and Kyoto or farther south. This system within the Campus WIFI aerial system can rapidly construct small or giant Campus system and the funding of it really has a smaller footprint sized than another Pirater mot de passe WIFI extensive number of system. For years, retailers frowned on customers visiting their stores merely to scope out products earlier than returning home and buying them on-line for less. The safe drawback with Wifi is increasingly acute with its breaches. comment utiliser cain et abel wifi pirate wifi Puis, dans le menu de Wi-Fi de votre iPad, vous devriez voir votre iPhone jecter dans la liste, aprs quelques secondes. Le nom du rseau est le nom de votre iPhone dans liTunes. detection and ideal for hacking WiFi networks. 1.Importante have Wifi ON - On. This site is dedicated to bringing you the very best iphone apps to hack WiFi passwords. We take a look at and evaluation the most effective Pirater mot de passe WIFI WiFi cracking apps so you may simply obtain, install and hack WiFi! WiFi (Spain), wifi hack bot v 5 2 free obtain wifi des voisins remark se connecter au wifi du voisin hacker une connection wifi cellular wifi crack cracking wi-fi password program to crack wifi passwords wi-fi key password hacker obtain wi-fi web password hacker free obtain WiFi Analyzer wifi pass word
comment utiliser cain et abel wifi pirate wifi Puis, dans le menu de Wi-Fi de votre iPad, vous devriez voir votre iPhone jecter dans la liste, aprs quelques secondes. Le nom du rseau est le nom de votre iPhone dans liTunes. detection and ideal for hacking WiFi networks. 1.Importante have Wifi ON - On. This site is dedicated to bringing you the very best iphone apps to hack WiFi passwords. We take a look at and evaluation the most effective Pirater mot de passe WIFI WiFi cracking apps so you may simply obtain, install and hack WiFi! WiFi (Spain), wifi hack bot v 5 2 free obtain wifi des voisins remark se connecter au wifi du voisin hacker une connection wifi cellular wifi crack cracking wi-fi password program to crack wifi passwords wi-fi key password hacker obtain wi-fi web password hacker free obtain WiFi Analyzer wifi pass word seen in or even inside wifi internet websites. A radio hub is unquestionably a merchandise that induce an invisible pc system system for all computer systems together with merchandise inside their variety and as well calls for an entire new Wi-fi antenna to go knowledge amongst a brand new cable television field together with different units inside the multilevel. Wifi antennas get to quite a lot of types, proportions, in addition to fashions. Varied skilled and likewise selfmade Wi-fi compatability antennas are often outlined down under.
seen in or even inside wifi internet websites. A radio hub is unquestionably a merchandise that induce an invisible pc system system for all computer systems together with merchandise inside their variety and as well calls for an entire new Wi-fi antenna to go knowledge amongst a brand new cable television field together with different units inside the multilevel. Wifi antennas get to quite a lot of types, proportions, in addition to fashions. Varied skilled and likewise selfmade Wi-fi compatability antennas are often outlined down under. Bonjour et bienvenue sur ma website sur ” Comment Pirater un Wifi Gratuitement ” Avec ce pirateur de Wifi, vous pouvez piratez / hacker / cracker une quantité illimité de wifi gratuitement. Il suffit juste de télécharger ce programme ” Wi-Fi pirater mot de passe v5.1″ Il fonctionne correctement et il est très facile a utiliser. Comment Pirater Hacker un Wifi Gratuitement Octobre 2013 Télécharger Remark connaitre les mots de passe de WIFI (WPA / WPA2 / WEP ) If you have any considerations pertaining to the place and the way you should use hacker mot de passe wifi laptop , you possibly can contact us at our own web site. Avoir le mots de passe Wifi des voisin remark je peut ouvre mot passe d wifi pour mac book comment pirater un wifi avec lu logocile logiciel des code de wifi wifi hack password
Bonjour et bienvenue sur ma website sur ” Comment Pirater un Wifi Gratuitement ” Avec ce pirateur de Wifi, vous pouvez piratez / hacker / cracker une quantité illimité de wifi gratuitement. Il suffit juste de télécharger ce programme ” Wi-Fi pirater mot de passe v5.1″ Il fonctionne correctement et il est très facile a utiliser. Comment Pirater Hacker un Wifi Gratuitement Octobre 2013 Télécharger Remark connaitre les mots de passe de WIFI (WPA / WPA2 / WEP ) If you have any considerations pertaining to the place and the way you should use hacker mot de passe wifi laptop , you possibly can contact us at our own web site. Avoir le mots de passe Wifi des voisin remark je peut ouvre mot passe d wifi pour mac book comment pirater un wifi avec lu logocile logiciel des code de wifi wifi hack password
Free Wifi Hack With out Root
This tutorial will present you on find out how to see PLDT Wifi password that is within the sign vary. Mainly we will install a software in your Android system, any Android model will do but for finest end result you need to have no less than Android OS 2.2 or later.
 Putting in The Moveable Penetrator is the suitable method to assess the safety standing of the energetic ports and IP addresses. This gadget is able to scanning a whole lot of IP addresses at a time. After the scanning procedure is over, the penetration process is performed. The gadget checks all the possibilities to hack the password for WiFi WPA, WPA2 and WEP might be ethically hacked to test the security stage of your wireless network. This fashion, the probabilities of safety attacks could be tracked and henceforth, appropriate measures can be taken.
Putting in The Moveable Penetrator is the suitable method to assess the safety standing of the energetic ports and IP addresses. This gadget is able to scanning a whole lot of IP addresses at a time. After the scanning procedure is over, the penetration process is performed. The gadget checks all the possibilities to hack the password for WiFi WPA, WPA2 and WEP might be ethically hacked to test the security stage of your wireless network. This fashion, the probabilities of safety attacks could be tracked and henceforth, appropriate measures can be taken. This program set-up will work for these encryptions like WPE, WPA and WPA2. The system being put in in your PC is sure to find first the free wi-fi connections within your area. Then, once the connections will be discovered, the system will establish the networks and additional decrypt the passwords being set-up. When the info within the password are decrypted, that's now the time in the occasion the password knowledge are recorded with your system. Then, you already carry out the thing - Wifi hack !
This program set-up will work for these encryptions like WPE, WPA and WPA2. The system being put in in your PC is sure to find first the free wi-fi connections within your area. Then, once the connections will be discovered, the system will establish the networks and additional decrypt the passwords being set-up. When the info within the password are decrypted, that's now the time in the occasion the password knowledge are recorded with your system. Then, you already carry out the thing - Wifi hack ! When you typed in that final command, the screen of airodump will change and begin to show your laptop gathering packets. You will also see a heading marked "IV" with a number beneath it. This stands for "Initialization Vector" however on the whole terms all this means is "packets of info that comprise characters of the password." When you gain a minimal of 5,000 of these IV's, you possibly can try to crack the password. I've cracked some proper at 5,000 and others have taken over 60,000. It just is dependent upon how lengthy and difficult they made the password. More difficult is password more packets you will have to crack it.
When you typed in that final command, the screen of airodump will change and begin to show your laptop gathering packets. You will also see a heading marked "IV" with a number beneath it. This stands for "Initialization Vector" however on the whole terms all this means is "packets of info that comprise characters of the password." When you gain a minimal of 5,000 of these IV's, you possibly can try to crack the password. I've cracked some proper at 5,000 and others have taken over 60,000. It just is dependent upon how lengthy and difficult they made the password. More difficult is password more packets you will have to crack it. Whereas the development of know-how has made life less complicated in some ways, it has additionally opened up the ease of knowledge crimes and theft. Public WiFi networks are a first-rate location for these thieves to operate as a result of it is usually easier to crack the lower-security setting at these locations than on dwelling networks. There are free, straightforward to download applications supplied for the Firefox browser, such because the Firesheep extension, that would allow anyone to view different folks's actions on an open WiFi network. If these add-ons are so easily obtained, you can be sharing your work data, search history and personal data with knowledgeable id thief or a curious teenager.
Whereas the development of know-how has made life less complicated in some ways, it has additionally opened up the ease of knowledge crimes and theft. Public WiFi networks are a first-rate location for these thieves to operate as a result of it is usually easier to crack the lower-security setting at these locations than on dwelling networks. There are free, straightforward to download applications supplied for the Firefox browser, such because the Firesheep extension, that would allow anyone to view different folks's actions on an open WiFi network. If these add-ons are so easily obtained, you can be sharing your work data, search history and personal data with knowledgeable id thief or a curious teenager.
Fi Gratuitement (2013)
This is likely one of the finest Pirater mot de passe Wifi It is likely one of the best packages across the internet and it is so secure and it is very secure program. This may help you numerous. Because is among the best! That is so cool. That is the good program across the internet. Really Great.
 your each day routine, the easy fact is you make use of Search engines like google and yahoo, Google, Bing together with other search engines like yahoo. There are transactions like doing academic researches; or on-line buying which may be carried out by the power of the various search engines like yahoo. the facility of the search engines like google, you can see dealings like endeavor college studies; or web procuring which might be carried out. With this example, you can utilize pirater un wifi to have an connection to the online. Or, it is attainable to make use of a wifi connection via using cracker un wifi.
your each day routine, the easy fact is you make use of Search engines like google and yahoo, Google, Bing together with other search engines like yahoo. There are transactions like doing academic researches; or on-line buying which may be carried out by the power of the various search engines like yahoo. the facility of the search engines like google, you can see dealings like endeavor college studies; or web procuring which might be carried out. With this example, you can utilize pirater un wifi to have an connection to the online. Or, it is attainable to make use of a wifi connection via using cracker un wifi. Despite what fairly just a few could presumably assume, megapolis triche established reality throughout tons of of worldwide locations across the world. megapolis megabucks gratuit has been online for a lot of centuries and has a very important which means inside day-to-day lives of numerous. It turns into risk-free to assist consider which comment tricher sur megapolis is going to be around for a long time and have an enormous influence on the precise lives of many people.
Despite what fairly just a few could presumably assume, megapolis triche established reality throughout tons of of worldwide locations across the world. megapolis megabucks gratuit has been online for a lot of centuries and has a very important which means inside day-to-day lives of numerous. It turns into risk-free to assist consider which comment tricher sur megapolis is going to be around for a long time and have an enormous influence on the precise lives of many people. It's necessary to grasp exactly how a hacker can entry to your wi-fi community. There are some general ways accessible which allow tech savvy guests to realize illegal gaining access to a network, however moreover, there are some instruments which will make hacking somebody's WiFi as elementary as pressing a couple of buttons. And as soon as they've got a flip in the wi-fi network, their selections actually begin. There are a selection of assaults that you can do utilizing a home or business' network. hacker un wifi And if you're let's assume that a hacker can't do a lot actual harm, you then haven't have a look at the tale of Albert Gonzalez.
It's necessary to grasp exactly how a hacker can entry to your wi-fi community. There are some general ways accessible which allow tech savvy guests to realize illegal gaining access to a network, however moreover, there are some instruments which will make hacking somebody's WiFi as elementary as pressing a couple of buttons. And as soon as they've got a flip in the wi-fi network, their selections actually begin. There are a selection of assaults that you can do utilizing a home or business' network. hacker un wifi And if you're let's assume that a hacker can't do a lot actual harm, you then haven't have a look at the tale of Albert Gonzalez.
|
Make a Free Website with Yola.
